Setting Up Azure AD SSO and SCIM
Configure automatic user provisioning through Microsoft Azure AD (Entra ID). Users are created, updated, and deactivated automatically based on your Microsoft 365 directory.
When to use this method
- You use Microsoft 365 / Azure AD (Entra ID)
- You want users to log in with their existing work credentials
- You want automatic user creation when new employees join
- You want automatic deactivation when employees leave
- You have 50+ users and want to reduce admin overhead
👤 Who Should Do This
A Microsoft 365 administrator with Global Admin or Application Admin rights.
Overview
🔐 Single Sign-On (SSO)
Staff log into TrainMeUK using their Microsoft 365 work account — no extra passwords.
- One password for all work apps
- Improved security with MFA
- 70% reduction in IT support tickets
👥 SCIM Provisioning
Automatically syncs user accounts from Microsoft 365 to TrainMeUK.
- Auto-create users when they join
- Auto-update details when they change
- Auto-deactivate when they leave
Note
Part 1: Setting Up SSO
In TrainMeUK: Get the Redirect URI
- Go to Admin → Settings → SSO & Provisioning
- Copy the Redirect URI shown on screen
- Keep this page open — you'll paste values back here later
In Microsoft Entra ID: Create App Registration
- Go to entra.microsoft.com → App registrations → New registration
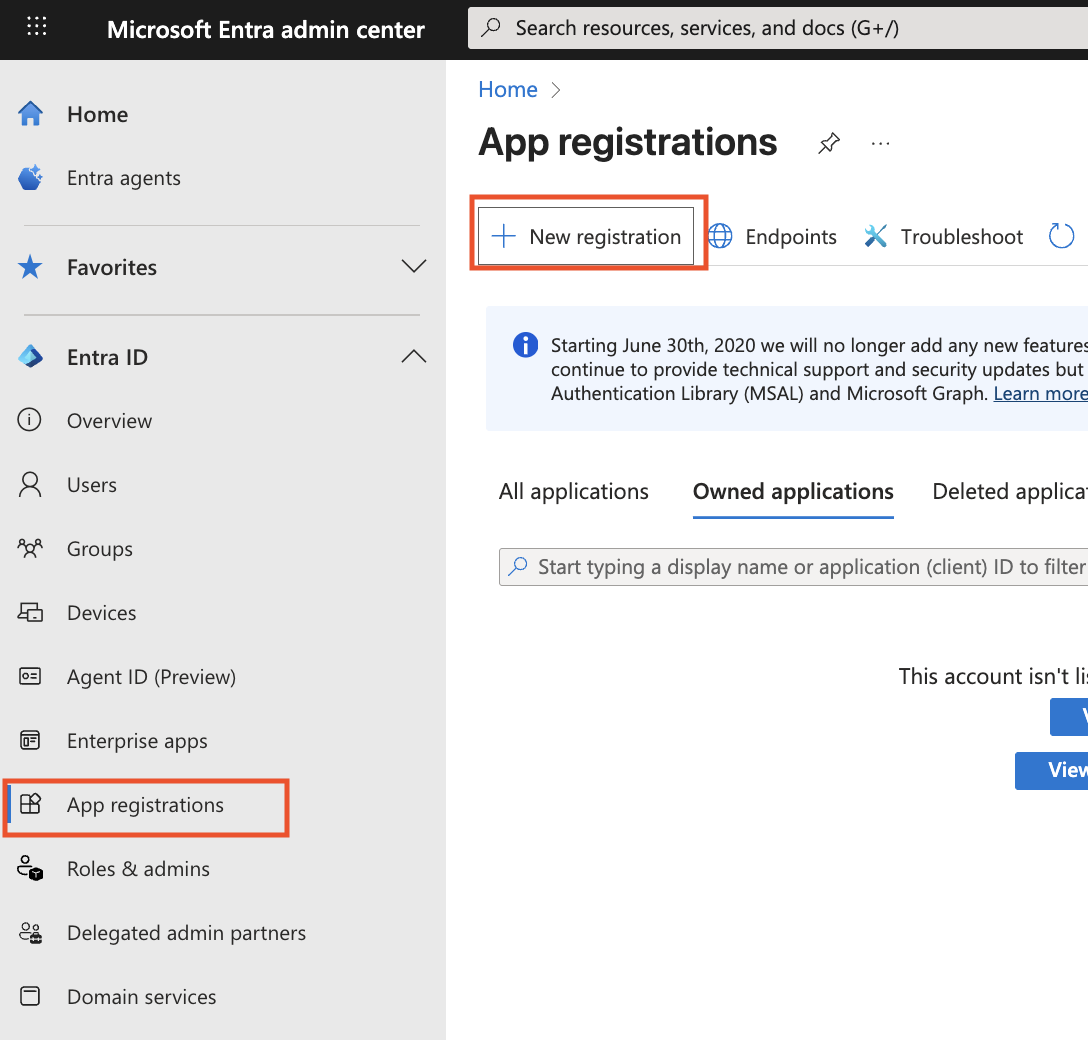
- Enter:
- Name: TrainMeUK SSO
- Supported account types: Accounts in this organisational directory only (Single tenant)
- Redirect URI: Paste the Redirect URI you copied from TrainMeUK
- Click Register
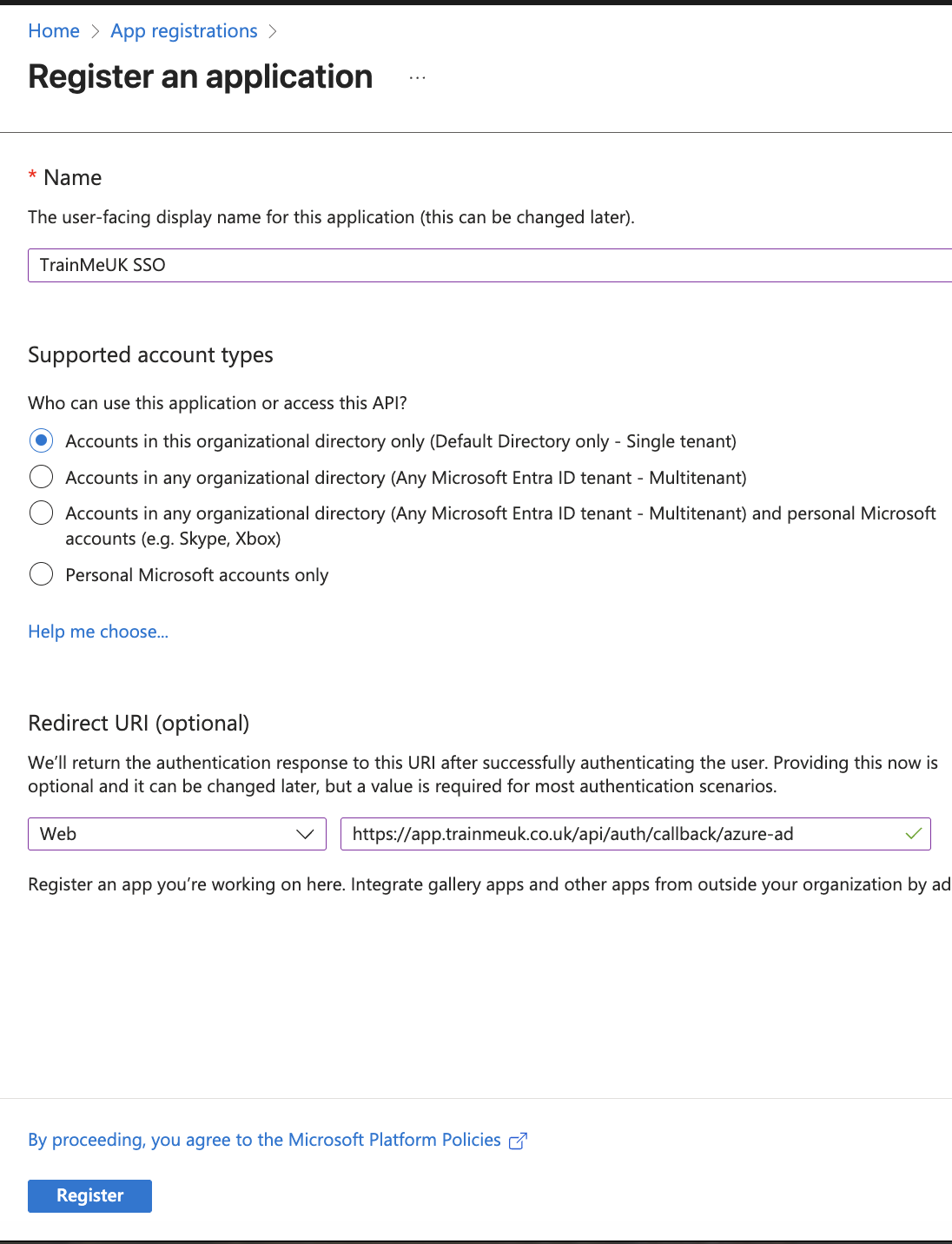
Collect Details from Microsoft
From the app you just created in App registrations:
| What to Copy | Where to Find It | Use In TrainMeUK |
|---|---|---|
| Application (client) ID | Overview page | Client ID |
| Directory (tenant) ID | Overview page | Tenant ID |
| Client secret value | Certificates & secrets → New client secret | Client Secret |
Tip
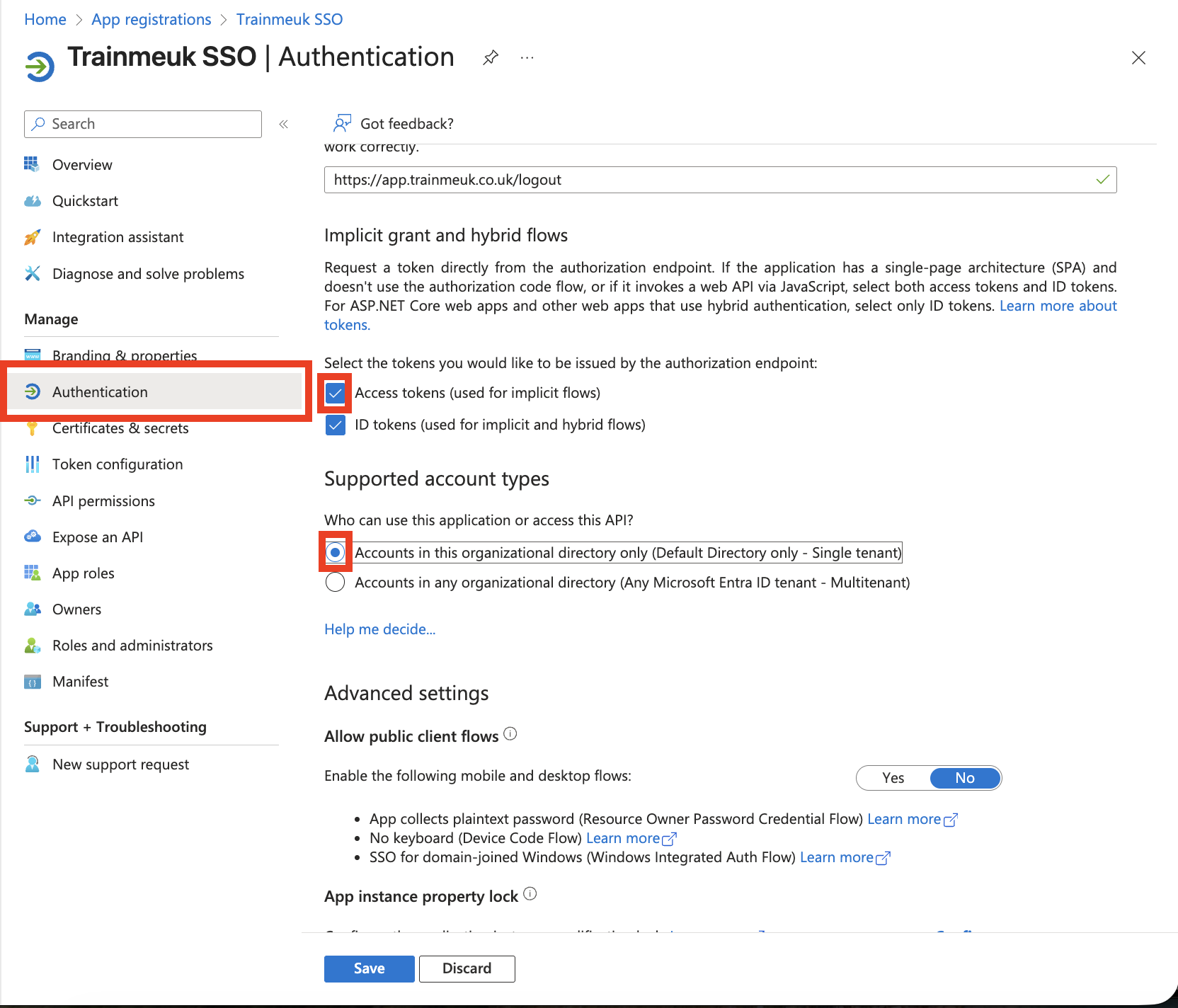
Enable ID Tokens
- In your app registration, go to Authentication
- Under "Implicit grant and hybrid flows", tick ID tokens
- Click Save
Back in TrainMeUK: Enable SSO
- Paste the values you collected:
- Tenant ID → from Directory (tenant) ID
- Client ID → from Application (client) ID
- Client Secret → the secret value you created
- Click Enable SSO
- Click Save
Test SSO
- Log out of TrainMeUK
- Click Sign in with Microsoft
- Use a normal staff account → you should go straight in ✅
Part 2: Setting Up SCIM Provisioning
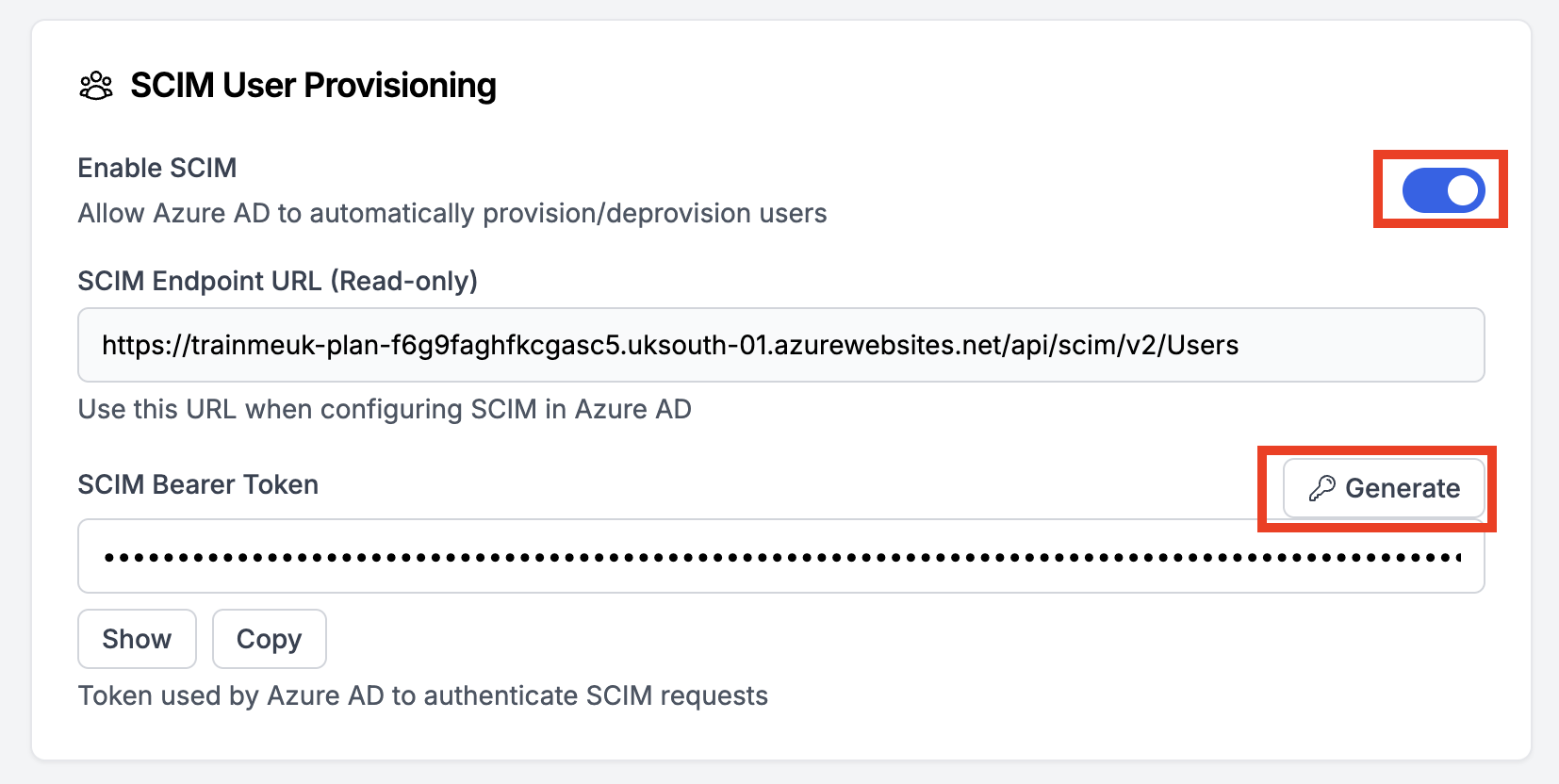
In TrainMeUK: Enable SCIM
- Go to Admin → Settings → SSO & Provisioning
- Toggle Enable SCIM on
- Copy the SCIM Endpoint URL
- Copy the SCIM Bearer Token (use the Copy button)
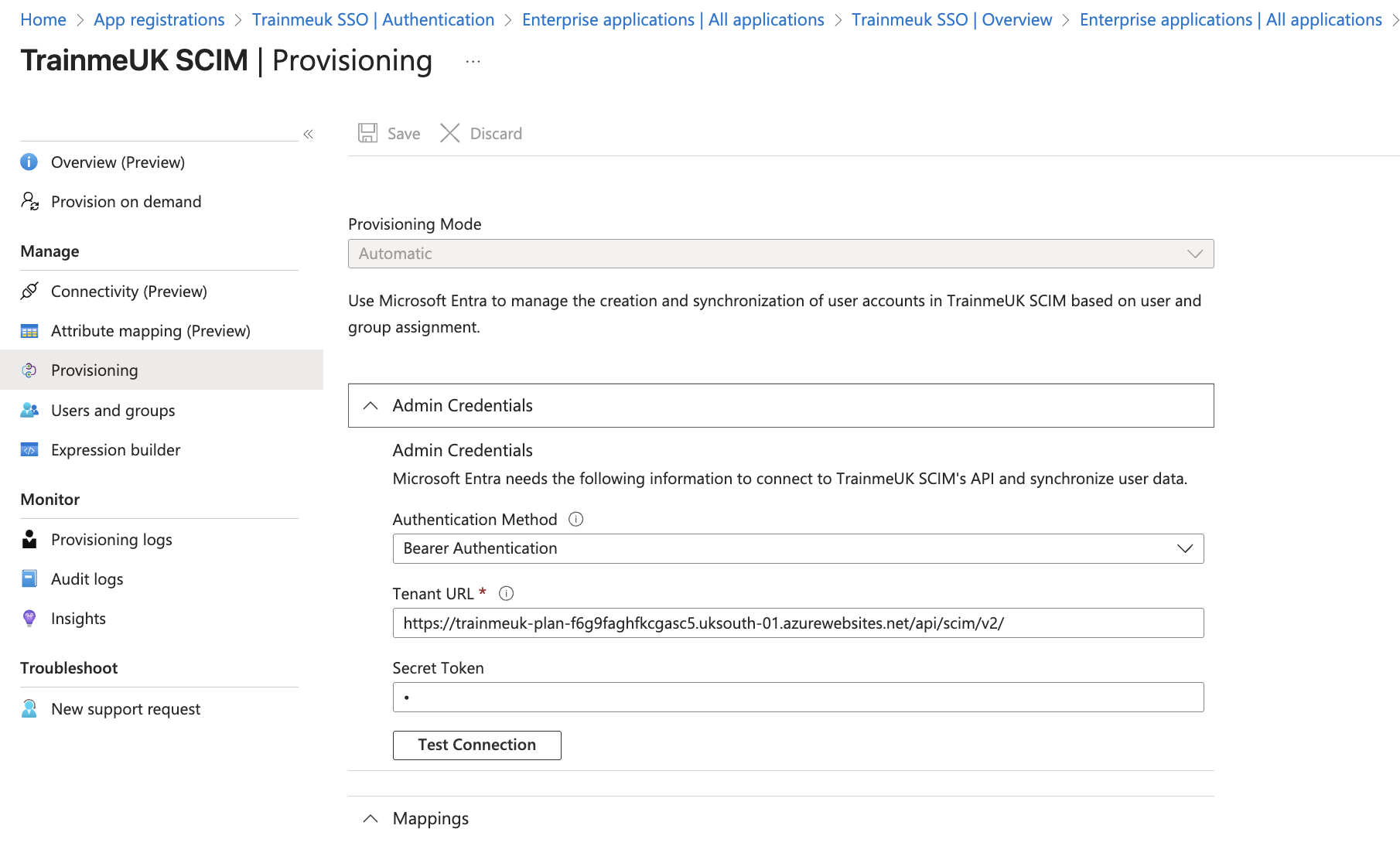
In Microsoft Entra ID: Configure Provisioning
- Go to entra.microsoft.com → Enterprise applications
- Open the app you registered for TrainMeUK SSO
- Go to Provisioning → Get started
- Set Provisioning Mode to Automatic
- Paste the values from TrainMeUK:
- Tenant URL → SCIM Endpoint URL
- Secret Token → SCIM Bearer Token
- Click Test connection → it should say Success
- Click Save
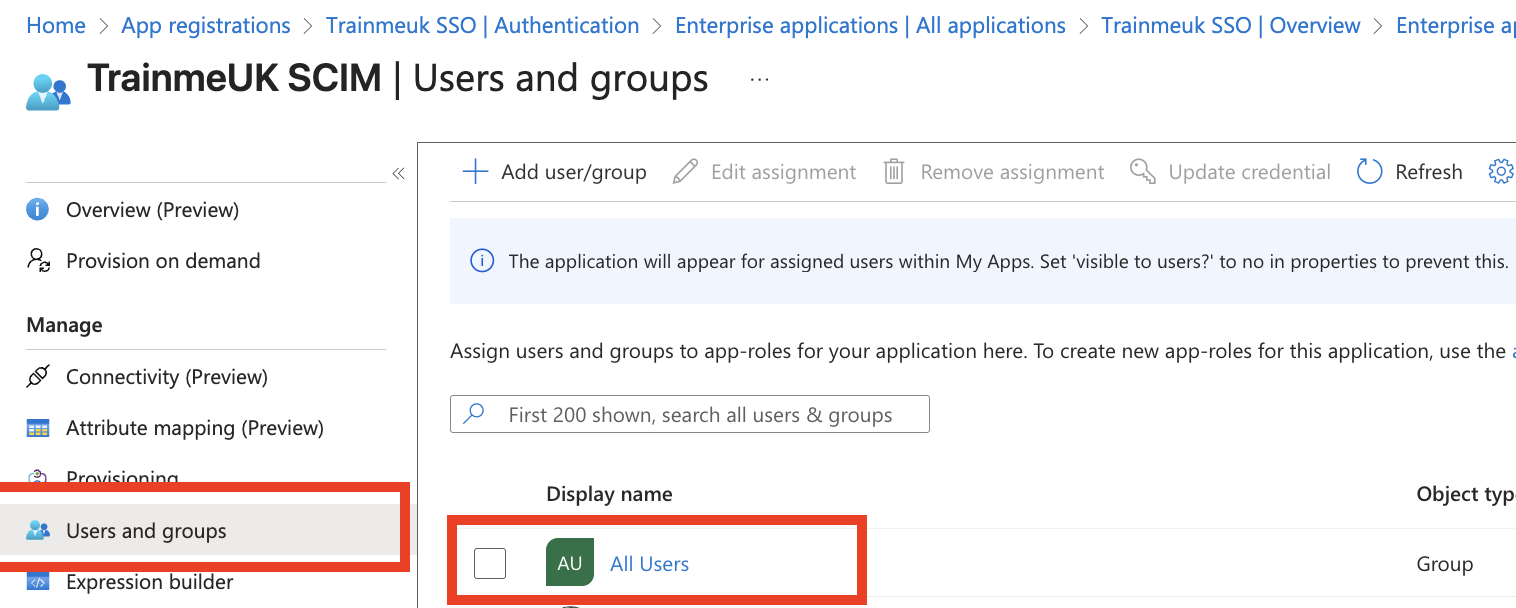
Choose Who Syncs
- In the TrainMeUK app in Entra, go to Users and groups
- Add the groups or people who should get TrainMeUK accounts
Tip
Start Provisioning
- Go back to Provisioning
- Click Start provisioning
- Entra will now keep TrainMeUK automatically in sync with Microsoft 365
Test SCIM
- Add a test user to the group you assigned
- Wait up to 40 minutes for sync (or force a sync in Provisioning)
- In TrainMeUK go to Admin → User Management
- The test user should appear ✅
What Happens Automatically
| Event | What Happens in TrainMeUK |
|---|---|
| New employee added to Microsoft 365 | User account automatically created, welcome email sent |
| Employee details change (department, title) | User profile automatically updated |
| Employee removed or disabled in Microsoft 365 | User account automatically deactivated |
| Employee role changes | Department and job title updated automatically |
Troubleshooting
"Needs admin approval" error
A Microsoft admin must log in once to approve the connection. After the first admin approval, all users can use SSO.
Redirect error during SSO login
Check the Redirect URI in TrainMeUK and Microsoft Entra ID match exactly, including https:// and any trailing slashes.
SCIM test connection fails
Check the SCIM Endpoint URL and Bearer Token are copied exactly from TrainMeUK. Ensure SCIM is enabled in TrainMeUK settings.
User doesn't appear after SCIM sync
Confirm the user is in the assigned group in Microsoft 365. Check the Provisioning logs in Entra ID for any errors.
📚 Detailed Setup Guides
For more detailed instructions with screenshots, see our comprehensive guides:
Related Guides
- Add Users Individually - For users not covered by SSO/SCIM
- User Roles & Permissions - Configure access levels for provisioned users
- Password Policy & MFA - Security settings (MFA is handled by Azure AD with SSO)