Password Policy & MFA
Configure password requirements and multi-factor authentication
Overview
Security settings control:
- Password complexity requirements
- Password expiry and history
- Account lockout policies
- Multi-factor authentication options
These settings apply organisation-wide.
Accessing Security Settings
Open Admin Settings
- Log in as an Admin (with appropriate permissions)
- Go to Admin → Settings
- Select the Security tab
Password Policy Settings
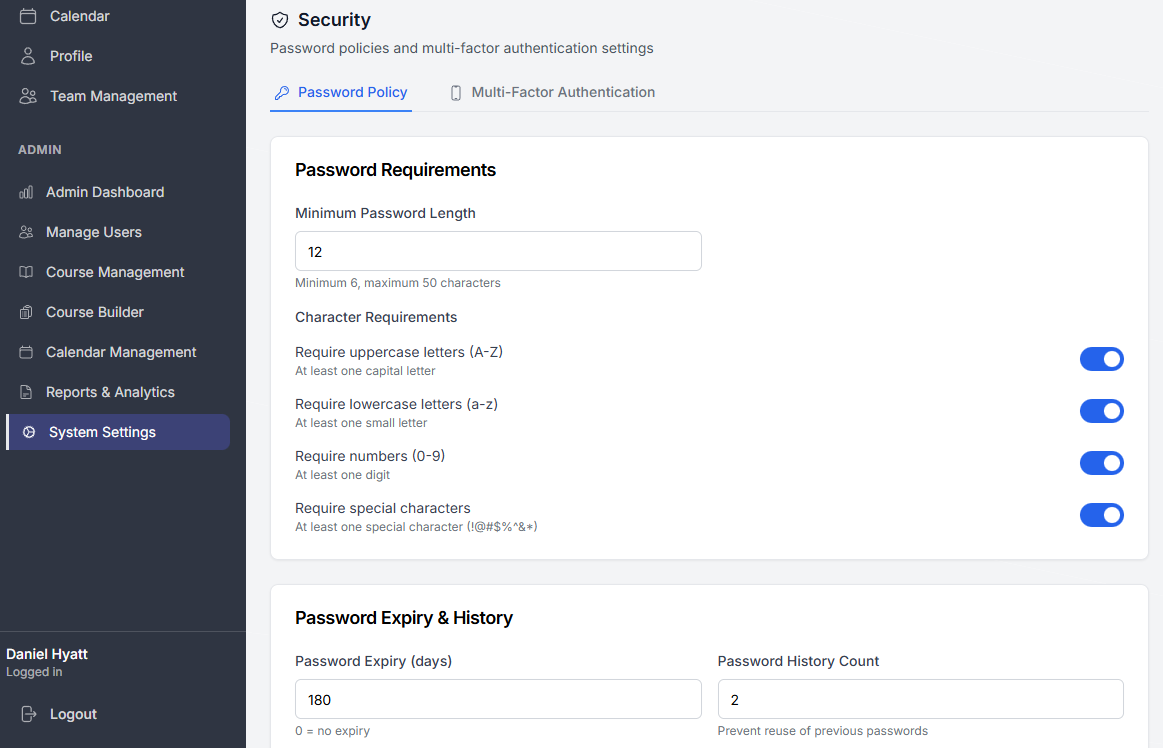
Password Complexity
Control what passwords must contain:
| Setting | Purpose | Recommended |
|---|---|---|
| Minimum Length | Shortest allowed password | 8-12 characters |
| Require Uppercase | Must contain A-Z | Yes |
| Require Lowercase | Must contain a-z | Yes |
| Require Numbers | Must contain 0-9 | Yes |
| Require Special Characters | Must contain !@#$% etc. | Optional |
Configuring Password Complexity
- Navigate to Security Settings
- Find the Password Policy section
- Set your requirements: enter minimum length, toggle on/off required character types
- Click Save
Password Age
Control how long passwords remain valid:
| Setting | Purpose | Example |
|---|---|---|
| Maximum Password Age | Days until password expires | 90 days |
| Password Never Expires | Disable expiry | Toggle on/off |
Password History
Prevent reuse of recent passwords:
| Setting | Purpose | Example |
|---|---|---|
| Remember Previous Passwords | How many old passwords to block | 5 passwords |
Account Lockout Settings
Protect against brute-force attacks:
| Setting | Purpose | Recommended |
|---|---|---|
| Failed Login Attempts | Attempts before lockout | 5 |
| Lockout Duration | Minutes account is locked | 15-30 minutes |
| Reset Counter After | Minutes before counter resets | 15 minutes |
What Happens on Lockout
- User sees "Account locked" message
- Must wait for lockout period
- Or contact admin for manual unlock
Multi-Factor Authentication (MFA)
Add an extra layer of security beyond passwords.

MFA Options Available
| Method | Description |
|---|---|
| Authenticator App | TOTP codes from apps like Microsoft Authenticator |
| Email Code | One-time code sent via email |
| Backup Codes | One-time recovery codes |
Configuring MFA Settings
- In Security Settings, find Multi-Factor Authentication section
- Configure MFA Requirement: Optional or Required
- Enable/disable authenticator app option
- Enable/disable email verification codes
- Enable/disable backup codes
- Click Save
Tip
Step-by-Step: Enforcing MFA
Enable MFA Features
- Go to Security Settings
- Enable authenticator app and/or email codes
- Enable backup codes as recovery option
- Save
Set MFA as Required
- Find "MFA Required" setting
- Toggle to Required
- Save
Communicate to Users
Let users know:
- MFA is now required
- How to set it up
- Where to get help
What Users Experience
First Login After MFA Required
- User logs in with password
- Prompted to set up MFA
- Scans QR code with authenticator app
- Enters verification code to confirm
- Receives backup codes to save
- Future logins require code from app
Subsequent Logins
- Enter username and password
- Enter code from authenticator app
- Access granted
Best Practices
Password Policy
| Area | Recommendation |
|---|---|
| Length | 8-12 minimum |
| Complexity | Require upper, lower, and numbers |
| Expiry | 90 days (or never with MFA) |
| History | Remember last 5 passwords |
MFA
| Area | Recommendation |
|---|---|
| Requirement | Highly recommended for admins |
| Method | Authenticator app preferred |
| Backup | Always enable backup codes |
Account Lockout
| Area | Recommendation |
|---|---|
| Attempts | 5 failed attempts |
| Duration | 15-30 minutes |
Tip
Temporary Passwords
When admins create users with temporary passwords:
- Temporary passwords may bypass complexity requirements
- Users must change password on first login
- The new password must meet complexity requirements
This allows admins to create simple temporary passwords for new users.
Troubleshooting
User locked out
Wait for lockout period, or go to User Management and unlock manually. Check for suspicious activity.
User forgot MFA device
Use backup codes if they saved them. Admin can reset MFA in User Management. User sets up MFA again.
Password rejected as too simple
Check complexity requirements. Ensure all requirements are met. Try a longer, more complex password.
MFA code not working
Check device time is correct (TOTP is time-sensitive). Ensure using correct authenticator. Try a fresh code (they refresh every 30 seconds).
Need to disable MFA temporarily
Consider if really necessary. Admin can disable for specific user in emergency. Re-enable as soon as possible.
Compliance Considerations
Financial Services
Often require: MFA for all users, 90-day password expiry, Strong complexity requirements
Healthcare
Often require: Audit trails of access, Strong authentication, Session timeouts
Education
Requirements vary: Check Ofsted/regulatory requirements, Consider safeguarding access controls
Related Guides
- Creating Users - User account setup
- User Roles & Permissions - Access control settings
- Adding Frameworks - Compliance frameworks